Microsoft Entra ID (via Graph API)
Overview
Microsoft Entra ID (Graph API) is a cloud-based Identity and Rights management service. The service is developed and managed by Microsoft Corp.
- Vendor: Microsoft
- Supported environment: SaaS
- Detection based on: Telemetry
- Supported application or feature: Application logs, Authentication logs
- Supported events:
Scalability
This integration will collect the events through Microsoft Graph API, which is only recommended for small environments. We can suggest using next numbers in order to decide which integration to use:
-
Sign-ins per day: < 300,000
-
Sign-ins per second (peak): < 10/sec
-
Audit logs per day: < 100,000
-
Total logs/day: < 500,000
-
Total logs/day: 250,000 – 1,500,000
If your environment exceeds these numbers, we strongly recommend to use the Microsoft Entra ID / Azure AD integration (see Microsoft Entra ID)
Configure
How to create an app registration with proper permissions
To connect Microsoft Entra ID to Sekoia.io, you need to create an app registration with the necessary permissions to access Entra ID users and groups. Follow these steps:
-
Sign in to the Azure portal and navigate to Microsoft Entra ID.
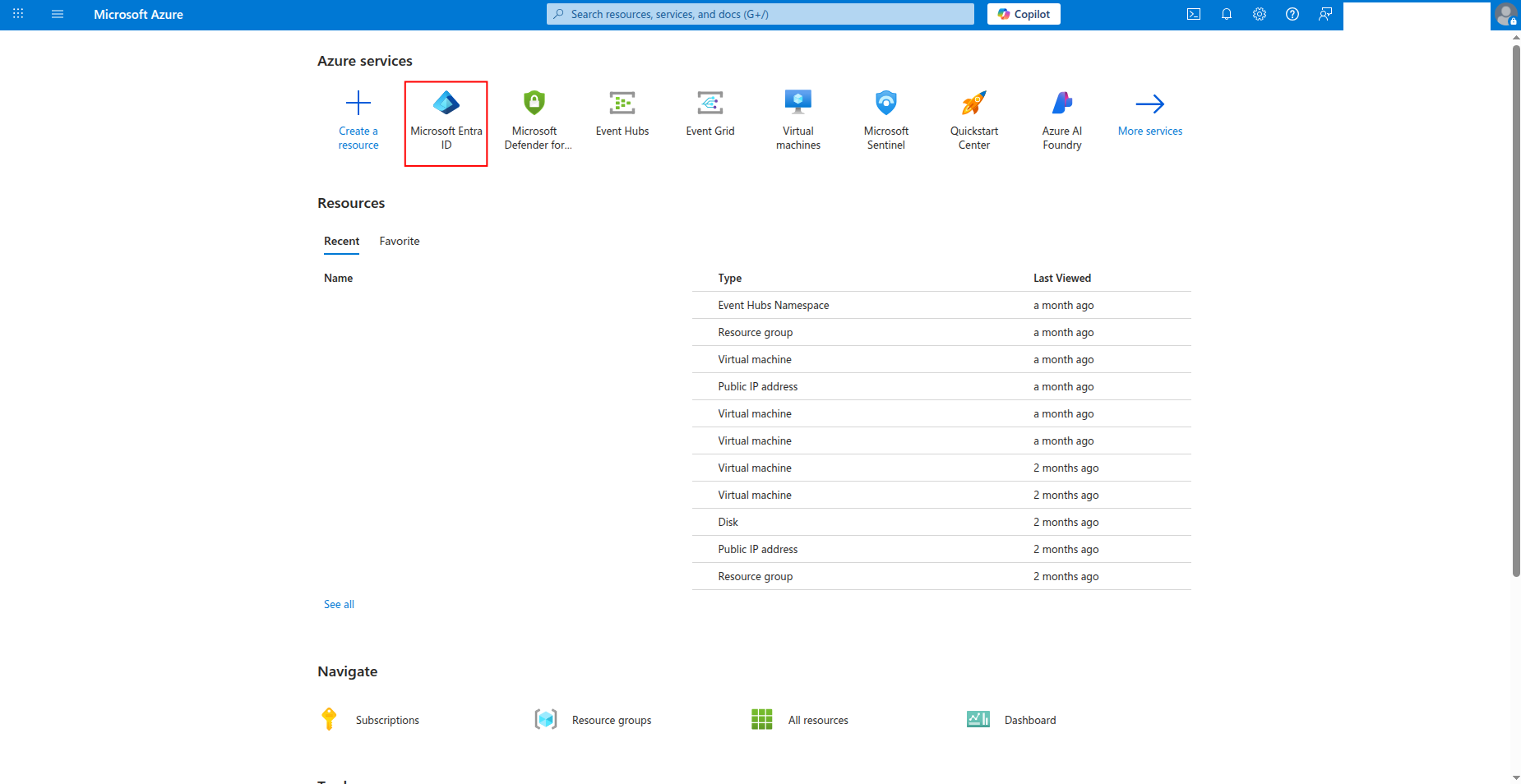
-
Click App registrations in the left navigation pane, then click New registration.
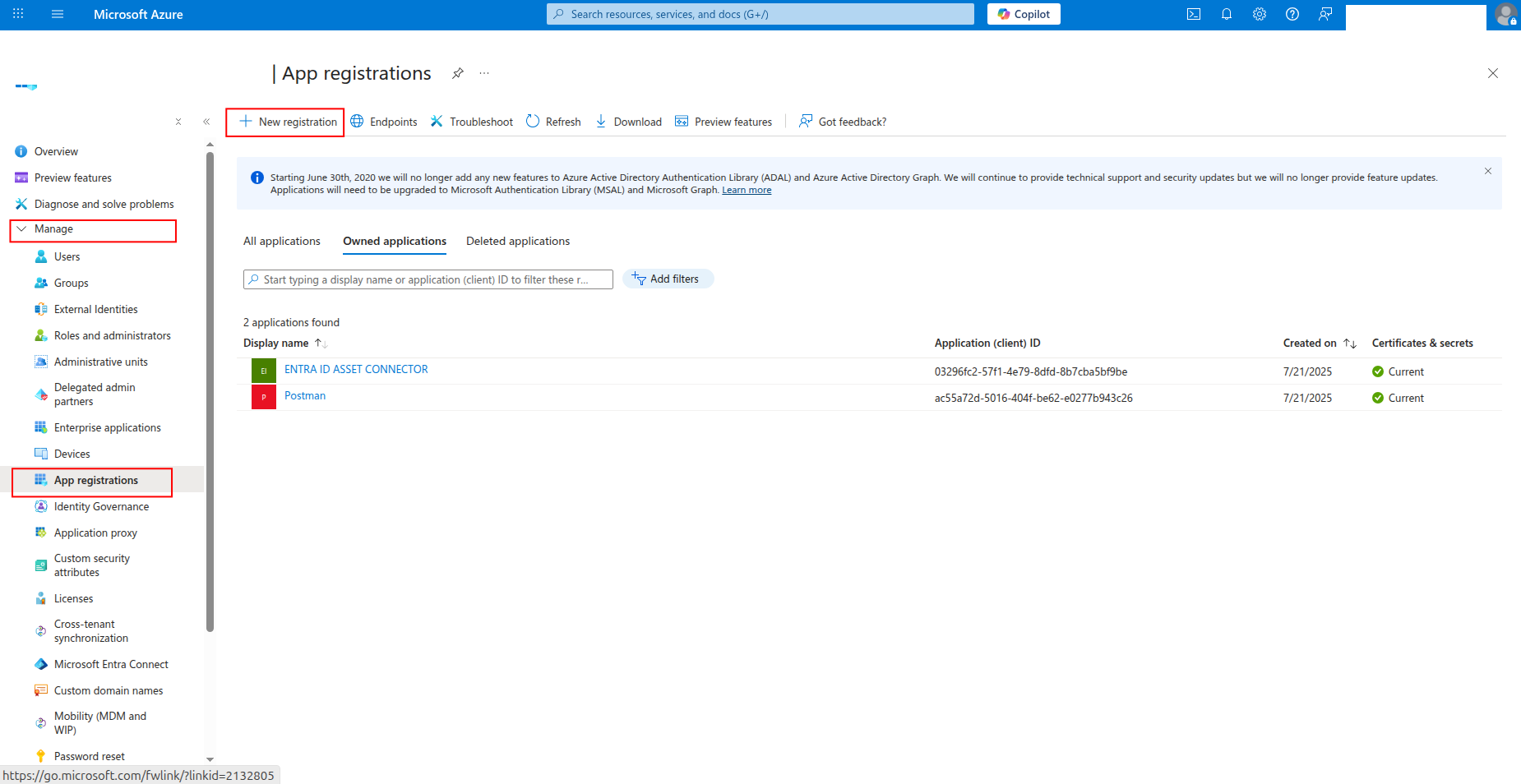
-
Enter a name for the application (e.g.,
sekoia-logs-reader) and click Register.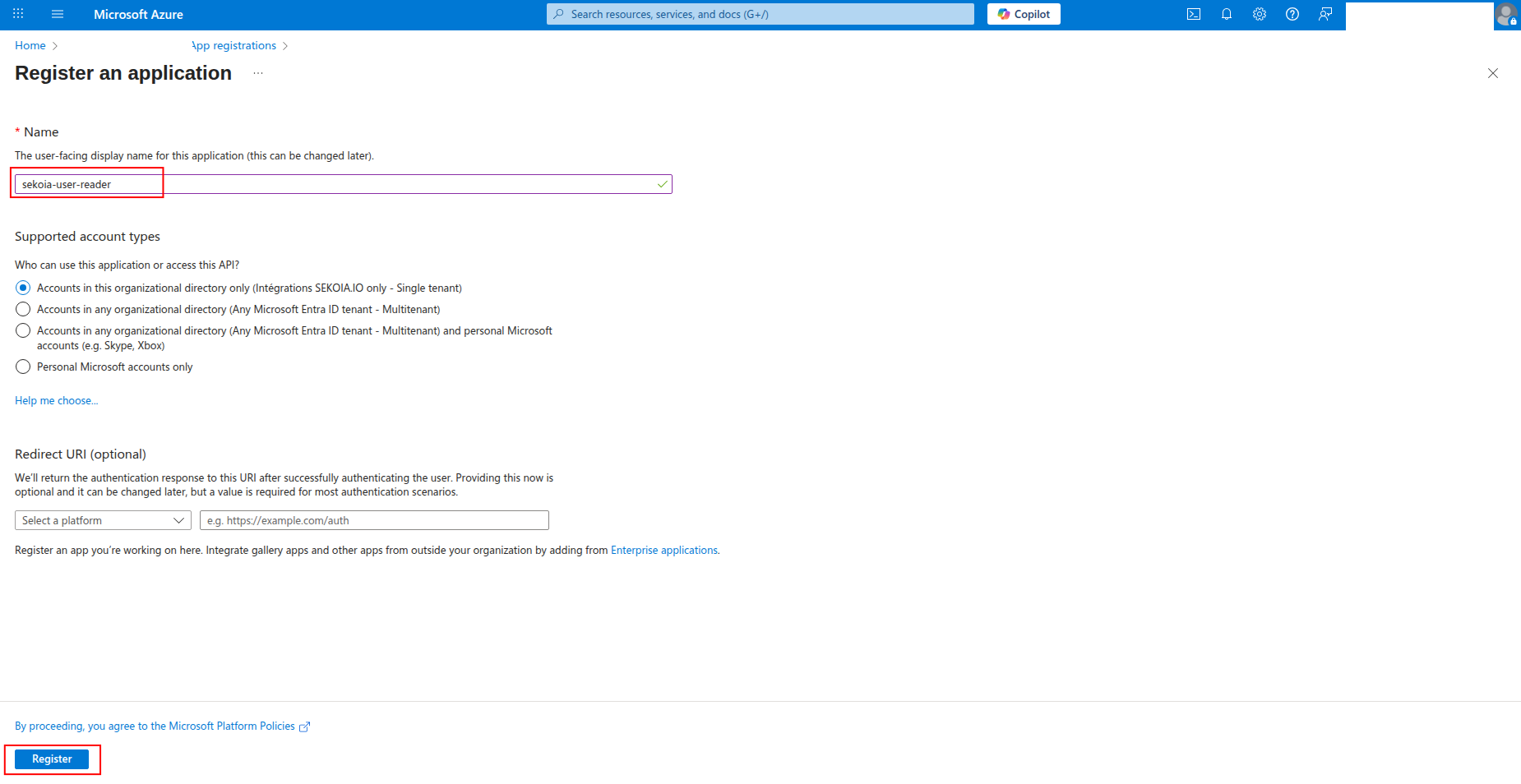
-
Copy the Application (client) ID and Directory (tenant) ID to a safe location. You'll need these values to configure the connector in Sekoia.io.
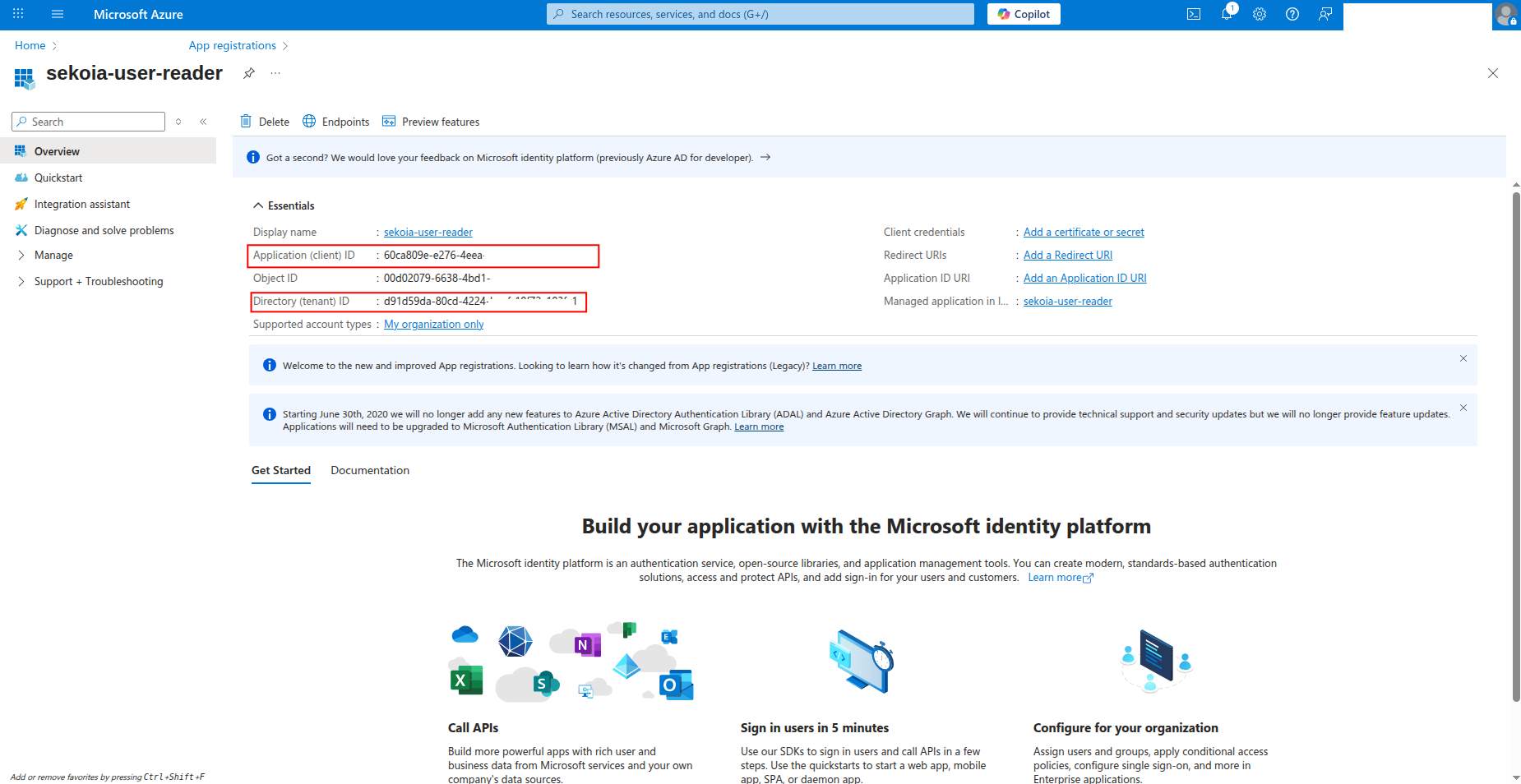
How to generate a client secret
After creating the app registration, you need to generate a client secret for authentication:
-
Click Certificates & secrets in the left navigation pane.
-
Click New client secret to generate a new secret.
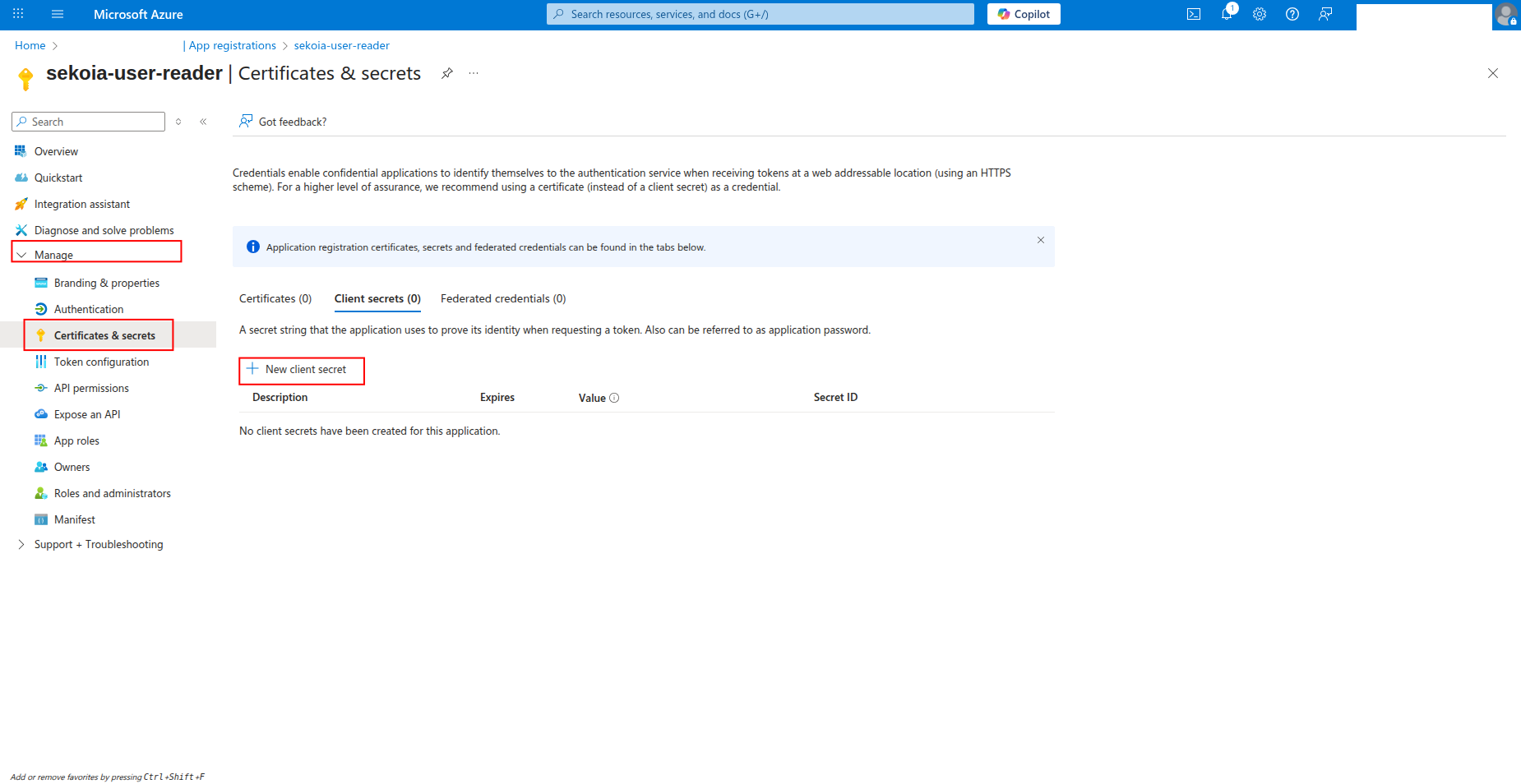
-
Enter a description for the secret (e.g.,
sekoia-connector-secret) and select an expiration period, then click Add.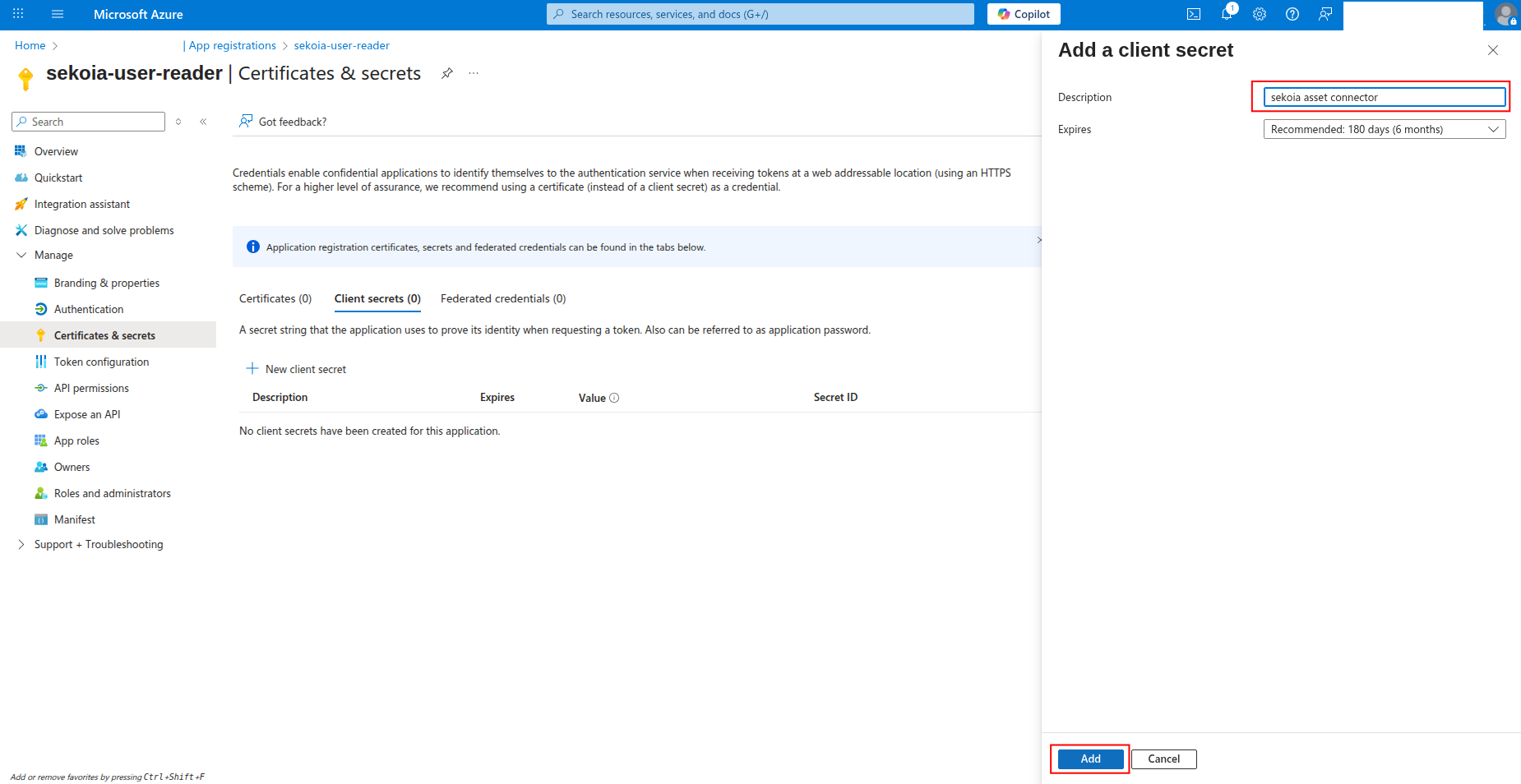
-
Copy the Value of the client secret to a safe location. You'll need this secret to configure the connector in Sekoia.io.
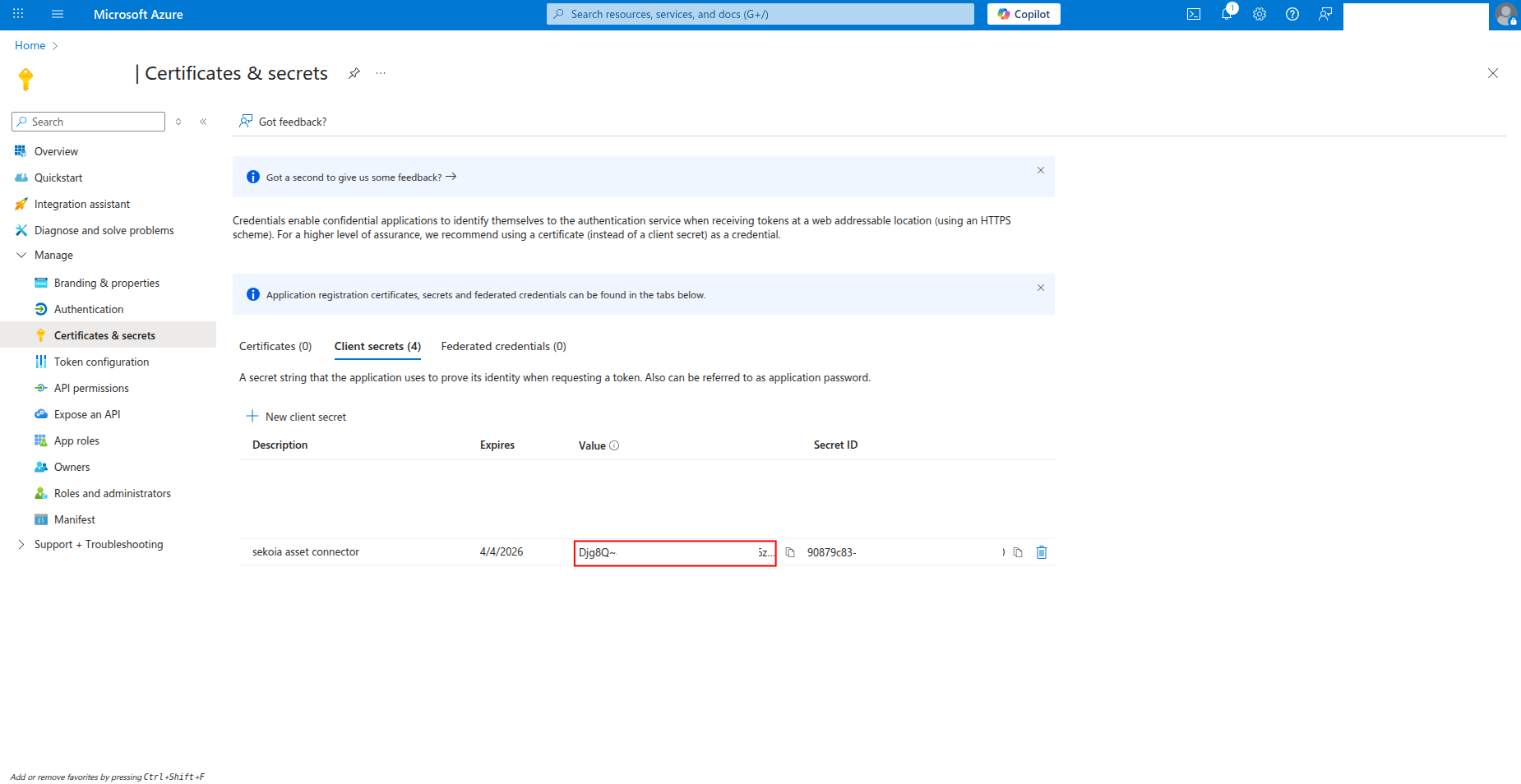
Warning
- The client secret value is only shown when you create it. If you lose it, you must create a new client secret.
- Store this secret securely and never share it publicly.
- Consider rotating client secrets regularly for security best practices.
Required API permissions
The app registration must have the following permissions to successfully fetch Entra ID users and groups:
{
"permissions": [
"AuditLog.Read.All",
"Directory.Read.All"
]
}
Required Permissions:
- AuditLog.Read.All: Read the log endpoint
- Directory.Read.All: Read directory data (optional, for advanced features)
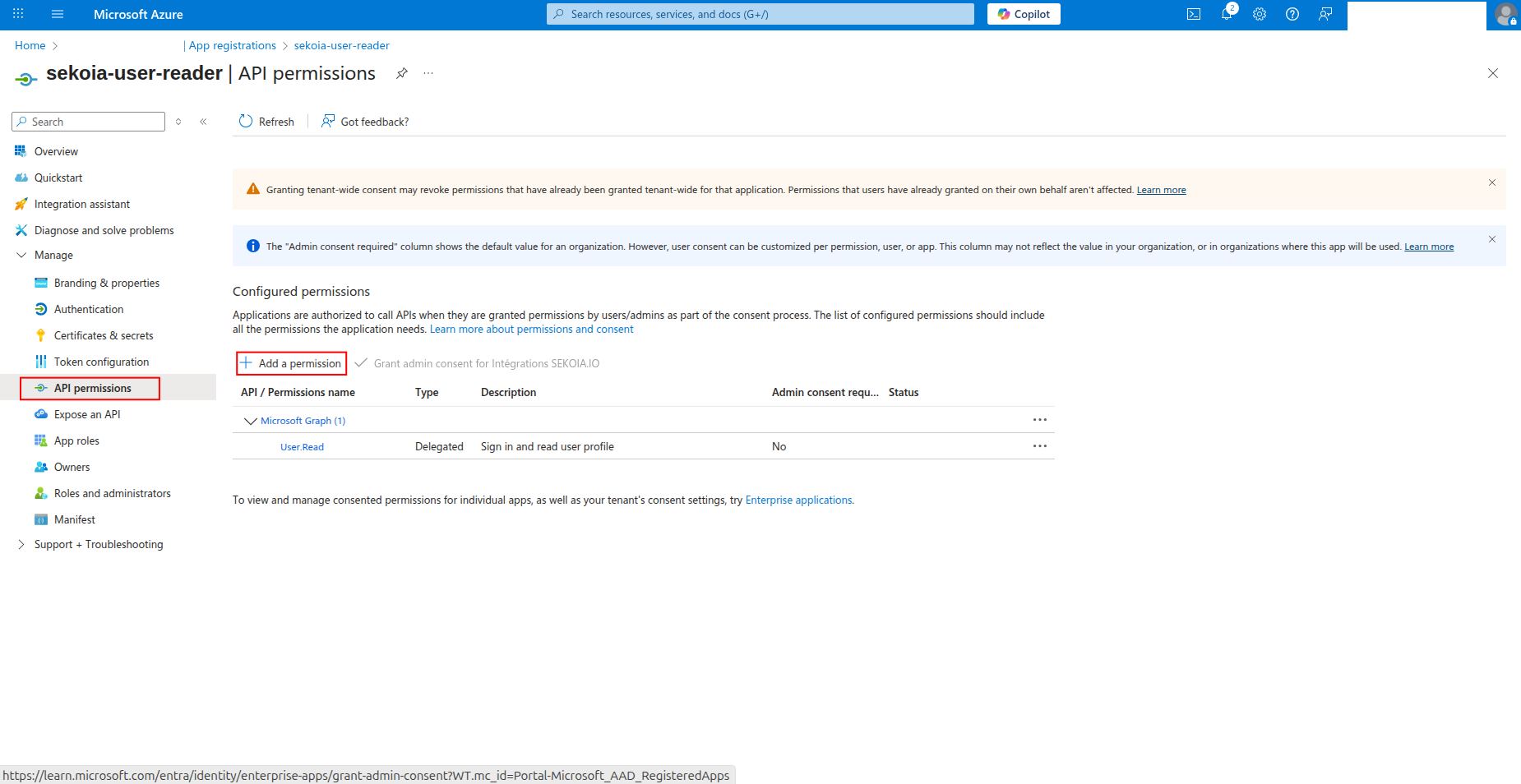
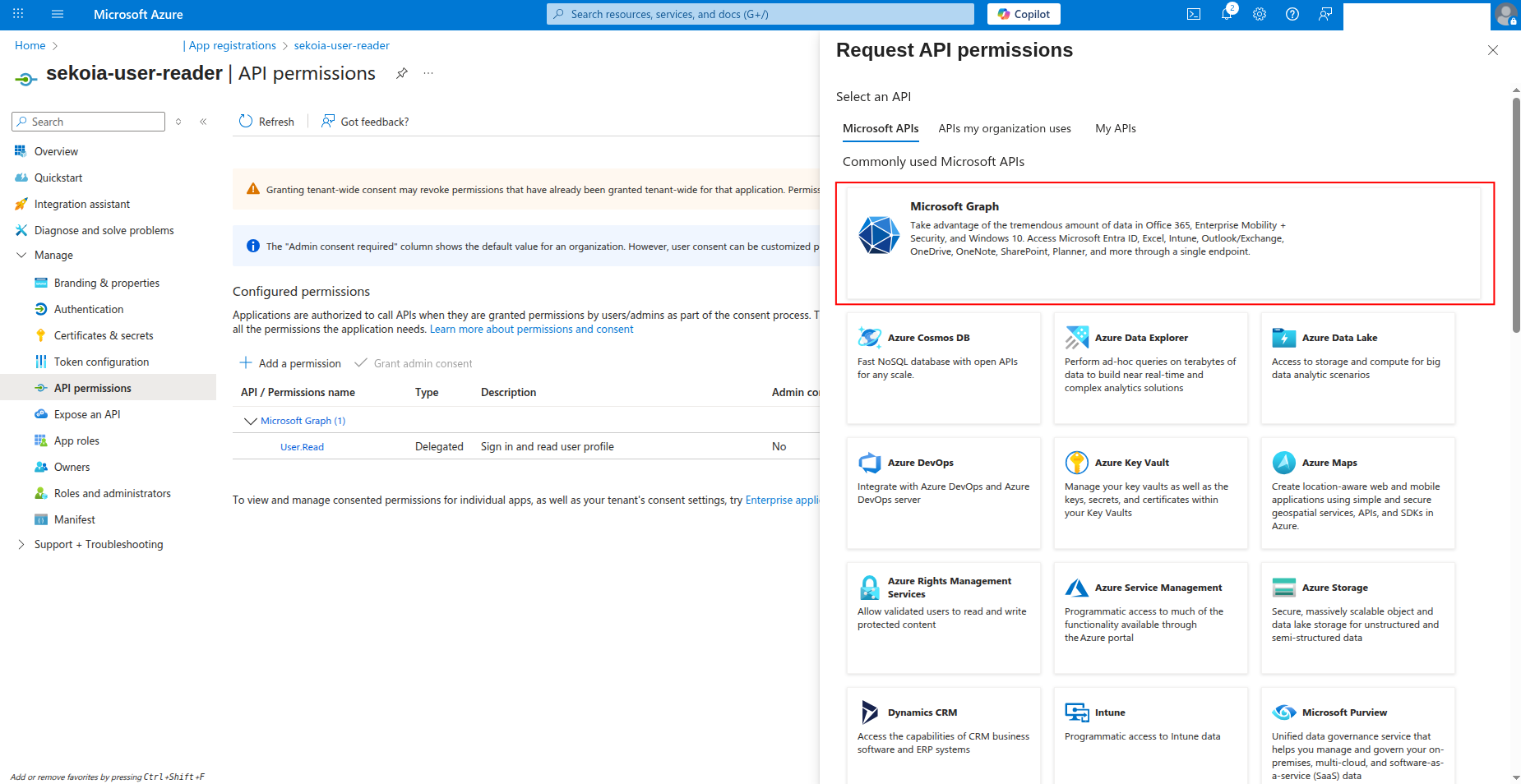
How to grant API permissions
To grant the required permissions to your app registration:
-
Click API permissions in the left navigation pane.
-
Click Add a permission to add new permissions.
-
Select Microsoft Graph as the API.
-
Select Application permissions and search for the required permissions:
AuditLog.Read.All-
Directory.Read.All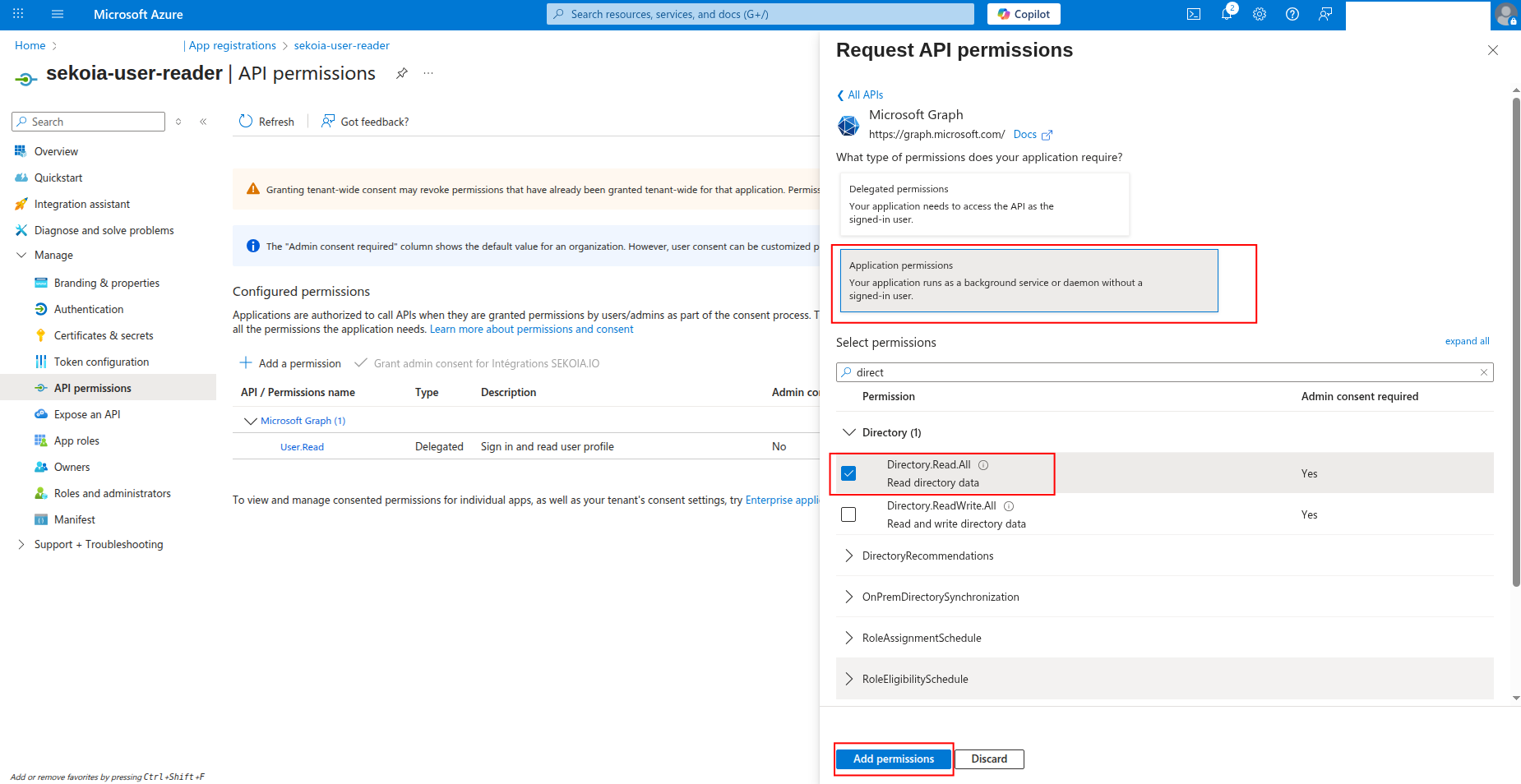
-
Click Add permissions to add the selected permissions.
-
Click Grant admin consent to grant the permissions (requires admin privileges).
Create your intake
- Go to the intake page and create a new intake from the
GraphAPI for Microsoft Entra ID / Azure AD. - Fill the form with the information collected during the app registration process.
Enjoy your events on the Events page
Detection section
The following section provides information for those who wish to learn more about the detection capabilities enabled by collecting this intake. It includes details about the built-in rule catalog, event categories, and ECS fields extracted from raw events. This is essential for users aiming to create custom detection rules, perform hunting activities, or pivot in the events page.
Related Built-in Rules
The following Sekoia.io built-in rules match the intake GraphAPI for Microsoft Entra ID / Azure AD. This documentation is updated automatically and is based solely on the fields used by the intake which are checked against our rules. This means that some rules will be listed but might not be relevant with the intake.
SEKOIA.IO x GraphAPI for Microsoft Entra ID / Azure AD on ATT&CK Navigator
Account Added To A Security Enabled Group
Detection in order to investigate who has added a specific Domain User in Domain Admins or Group Policy Creator Owners (Security event 4728)
- Effort: master
Account Removed From A Security Enabled Group
Detection in order to investigate who has removed a specific Domain User in Domain Admins or Group Policy Creator Owners (Security event 4729)
- Effort: master
Backup Catalog Deleted
The rule detects when the Backup Catalog has been deleted. It means the administrators will not be able to access any backups that were created earlier to perform recoveries. This is often being done using the wbadmin.exe tool.
- Effort: intermediate
Computer Account Deleted
Detects computer account deletion.
- Effort: master
Cryptomining
Detection of domain names potentially related to cryptomining activities.
- Effort: master
DHCP Server Error Failed Loading the CallOut DLL
This rule detects a DHCP server error in which a specified Callout DLL (in registry) could not be loaded.
- Effort: intermediate
DHCP Server Loaded the CallOut DLL
This rule detects a DHCP server in which a specified Callout DLL (in registry) was loaded. This would indicate a succesful attack against DHCP service allowing to disrupt the service or alter the integrity of the responses.
- Effort: intermediate
DNS Server Error Failed Loading The ServerLevelPluginDLL
This rule detects a DNS server error in which a specified plugin DLL (in registry) could not be loaded. This requires the dedicated Windows event provider Microsoft-Windows-DNS-Server-Service.
- Effort: master
Domain Trust Created Or Removed
A trust was created or removed to a domain. An attacker could perform that in order to do lateral movement easily between domains or shutdown the ability of two domains to communicate.
- Effort: advanced
Dynamic DNS Contacted
Detect communication with dynamic dns domain. This kind of domain is often used by attackers. This rule can trigger false positive in non-controlled environment because dynamic dns is not always malicious.
- Effort: master
Exfiltration Domain
Detects traffic toward a domain flagged as a possible exfiltration vector.
- Effort: master
Microsoft Defender Antivirus History Deleted
Windows Defender history has been deleted. Could be an attempt by an attacker to remove its traces.
- Effort: master
Microsoft Defender Antivirus Tampering Detected
Detection of Windows Defender Tampering, from definitions' deletion to deactivation of parts or all of Defender.
- Effort: advanced
Microsoft Defender Antivirus Threat Detected
Detection of a windows defender alert indicating the presence of potential malware
- Effort: advanced
Nimbo-C2 User Agent
Nimbo-C2 Uses an unusual User-Agent format in its implants.
- Effort: intermediate
Password Change On Directory Service Restore Mode (DSRM) Account
The Directory Service Restore Mode (DSRM) account is a local administrator account on Domain Controllers. Attackers may change the password to gain persistence.
- Effort: intermediate
Possible Replay Attack
This event can be a sign of Kerberos replay attack or, among other things, network device configuration or routing problems.
- Effort: master
Potential Bazar Loader User-Agents
Detects potential Bazar loader communications through the user-agent
- Effort: elementary
Potential Lemon Duck User-Agent
Detects LemonDuck user agent. The format used two sets of alphabetical characters separated by dashes, for example "User-Agent: Lemon-Duck-[A-Z]-[A-Z]".
- Effort: elementary
Remote Access Tool Domain
Detects traffic toward a domain flagged as a Remote Administration Tool (RAT).
- Effort: master
Remote Monitoring and Management Software - AnyDesk
Detect artifacts related to the installation or execution of the Remote Monitoring and Management tool AnyDesk.
- Effort: master
SEKOIA.IO Intelligence Feed
Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team.
- Effort: elementary
Sekoia.io EICAR Detection
Detects observables in Sekoia.io CTI tagged as EICAR, which are fake samples meant to test detection.
- Effort: master
TOR Usage Generic Rule
Detects TOR usage globally, whether the IP is a destination or source. TOR is short for The Onion Router, and it gets its name from how it works. TOR intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: master
User Account Created
Detects user creation on windows servers, which shouldn't happen in an Active Directory environment. Apply this on your windows server logs and not on your DC logs. One default account defaultuser0 is excluded as only used during Windows set-up. This detection use Security Event ID 4720.
- Effort: master
User Account Deleted
Detects local user deletion
- Effort: master
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
Authentication logs |
None |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "{\"id\":\"id\",\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"result\":\"success\",\"resultReason\":\"Successfully added member to group\",\"activityDisplayName\":\"Add member to group\",\"activityDateTime\":\"2018-01-09T21:20:02.7215374Z\",\"loggedByService\":\"Core Directory\",\"initiatedBy\":{\"user\":{\"id\":\"user1\",\"displayName\":\"user1\",\"userPrincipalName\":\"test@test.test\",\"ipAddress\":\"127.0.0.1\"},\"app\":null},\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"displayName\":\"testValue2\",\"Type\":\"Group\",\"modifiedProperties\":[{\"displayName\":\"testValue3\",\"oldValue\":null,\"newValue\":\"DirectorySync\"}],\"groupType\":\"unifiedGroups\"},{\"id\":\"00000000-0000-0000-0000-000000000000\",\"displayName\":null,\"Type\":\"User\",\"modifiedProperties\":[],\"userPrincipalName\":\"bob@contoso.com\"}],\"additionalDetails\":[{\"key\":\"Additional Detail Name\",\"value\":\"Additional Detail Value\"}]}",
"event": {
"action": "Add member to group",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2018-01-09T21:20:02.721537Z",
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"related": {
"ip": [
"127.0.0.1"
],
"user": [
"user1"
]
},
"service": {
"name": "Core Directory"
},
"source": {
"address": "127.0.0.1",
"ip": "127.0.0.1"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "test@test.test",
"id": "user1",
"name": "user1"
}
}
{
"message": "{\"id\":\"Device Registration Service_testestest_O9KWA_1044477278\",\"activityDateTime\":\"2025-11-12T13:50:16.693874+00:00\",\"activityDisplayName\":\"Recover device local administrator password\",\"additionalDetails\":[{\"key\":\"AdditionalInfo\",\"value\":\"Successfully recovered local credential by device id\"},{\"key\":\"Device Id\",\"value\":\"00000000-0000-0000-0000-000000000000\"}],\"category\":\"Device\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"user\":{\"id\":\"user1\",\"@odata.type\":\"#microsoft.graph.userIdentity\",\"userType\":null,\"homeTenantId\":null,\"homeTenantName\":null,\"ipAddress\":\"192.0.2.1\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}},\"loggedByService\":\"Device Registration Service\",\"operationType\":\"Get\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Device\"}]}",
"event": {
"action": "Recover device local administrator password",
"dataset": "Device",
"outcome": "success",
"provider": "Device Registration Service"
},
"@timestamp": "2025-11-12T13:50:16.693874Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Get"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"related": {
"ip": [
"192.0.2.1"
]
},
"service": {
"name": "Device Registration Service"
},
"source": {
"address": "192.0.2.1",
"ip": "192.0.2.1"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE",
"id": "user1"
}
}
{
"message": "{\"id\":\"Device Registration Service_00000000-0000-0000-0000-000000000000_XJROS_218764547\",\"activityDateTime\":\"2025-11-12T13:51:01.550249+00:00\",\"activityDisplayName\":\"Recover device local administrator password\",\"additionalDetails\":[{\"key\":\"AdditionalInfo\",\"value\":\"Successfully recovered local credential by device id\"},{\"key\":\"Device Id\",\"value\":\"00000000-0000-0000-0000-000000000000\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"user\":{\"id\":\"user1\",\"@odata.type\":\"#microsoft.graph.userIdentity\",\"userType\":null,\"homeTenantId\":null,\"homeTenantName\":null,\"ipAddress\":\"192.0.2.1\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}},\"loggedByService\":\"Device Registration Service\",\"operationType\":\"Get\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Device\"}]}",
"event": {
"action": "Recover device local administrator password",
"dataset": "Device",
"outcome": "success",
"provider": "Device Registration Service"
},
"@timestamp": "2025-11-12T13:51:01.550249Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Get"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"related": {
"ip": [
"192.0.2.1"
]
},
"service": {
"name": "Device Registration Service"
},
"source": {
"address": "192.0.2.1",
"ip": "192.0.2.1"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE",
"id": "user1"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_UM6H9_56092970\",\"activityDateTime\":\"2025-11-12T13:48:46.838399+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"ServerAd\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"ServerAd\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:48:46.838399Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_testestest_Q7H4G_311862498\",\"activityDateTime\":\"2025-11-12T14:06:02.898026+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"ServerAd\"}],\"category\":\"Device\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"ServerAd\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:06:02.898026Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149026\",\"activityDateTime\":\"2025-11-12T13:59:29.848568+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T12:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.848568Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T12:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149037\",\"activityDateTime\":\"2025-11-12T13:59:29.867566+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.867566Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T13:29:28Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149063\",\"activityDateTime\":\"2025-11-12T13:59:29.878565+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-10T17:54:14Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.878565Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-10T17:54:14Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149100\",\"activityDateTime\":\"2025-11-12T13:59:29.889567+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T10:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.889567Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T10:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149117\",\"activityDateTime\":\"2025-11-12T13:59:29.898566+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T11:59:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.898566Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T11:59:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149132\",\"activityDateTime\":\"2025-11-12T13:59:29.907567+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.907567Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T13:29:28Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149153\",\"activityDateTime\":\"2025-11-12T13:59:29.918566+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T10:59:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.918566Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T10:59:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149190\",\"activityDateTime\":\"2025-11-12T13:59:29.933565+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.933565Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T13:29:28Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149219\",\"activityDateTime\":\"2025-11-12T13:59:29.948567+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T12:59:28Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.948567Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T12:59:28Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149230\",\"activityDateTime\":\"2025-11-12T13:59:29.964563+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T11:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.964563Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T11:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149238\",\"activityDateTime\":\"2025-11-12T13:59:29.975564+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-07T14:53:10Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.975564Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-07T14:53:10Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149246\",\"activityDateTime\":\"2025-11-12T13:59:29.987564+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T08:53:09Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:29.987564Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T08:53:09Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149259\",\"activityDateTime\":\"2025-11-12T13:59:30.006565+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T09:55:30Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.006565Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T09:55:30Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149269\",\"activityDateTime\":\"2025-11-12T13:59:30.019566+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.019566Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T13:29:28Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149290\",\"activityDateTime\":\"2025-11-12T13:59:30.028567+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T10:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.028567Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T10:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149313\",\"activityDateTime\":\"2025-11-12T13:59:30.039564+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T11:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.039564Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T11:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149355\",\"activityDateTime\":\"2025-11-12T13:59:30.057567+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T10:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.057567Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T10:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149387\",\"activityDateTime\":\"2025-11-12T13:59:30.068569+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T12:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.068569Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T12:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149429\",\"activityDateTime\":\"2025-11-12T13:59:30.081568+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.081568Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T13:29:28Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149440\",\"activityDateTime\":\"2025-11-12T13:59:30.090567+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T09:23:11Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.090567Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T09:23:11Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149448\",\"activityDateTime\":\"2025-11-12T13:59:30.107567+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-10T14:54:14Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.107567Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-10T14:54:14Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149456\",\"activityDateTime\":\"2025-11-12T13:59:30.126568+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T10:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.126568Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T10:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149465\",\"activityDateTime\":\"2025-11-12T13:59:30.137568+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T11:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.137568Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-12T11:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149492\",\"activityDateTime\":\"2025-11-12T13:59:30.151564+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-08T04:23:13Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.151564Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:59:29Z\"]",
"oldValue": "[\"2025-11-08T04:23:13Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149500\",\"activityDateTime\":\"2025-11-12T13:59:30.202566+00:00\",\"activityDisplayName\":\"Delete device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Delete\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Delete device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.202566Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Delete"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_APC1W_25149517\",\"activityDateTime\":\"2025-11-12T13:59:30.251568+00:00\",\"activityDisplayName\":\"Add device\",\"additionalDetails\":[],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Add\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[true]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue3\",\"newValue\":\"[false]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue4\",\"newValue\":\"[\\\"00000000-0000-0000-0000-000000000000\\\"]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue5\",\"newValue\":\"[\\\"Windows\\\"]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue6\",\"newValue\":\"[\\\"ServerAd\\\"]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue7\",\"newValue\":\"[true]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue8\",\"newValue\":\"[\\\"MGPWZXVdvYvPPHl\\\"]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue9\",\"newValue\":\"[\\\"2025-11-12T13:59:30Z\\\"]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue10\",\"newValue\":\"\\\"AccountEnabled, CloudCreated, DeviceId, DeviceOSType, DeviceTrustType, DirSyncEnabled, DisplayName, LastDirSyncTime\\\"\"},{\"displayName\":\"testValue11\",\"newValue\":\"\\\"DirectorySync\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Add device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.251568Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Add"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_2U6UD_332536708\",\"activityDateTime\":\"2025-11-12T13:42:30.543541+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"AzureAd\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"1.0\\\"]\",\"oldValue\":\"[\\\"10.0.22631.2715\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"[\\\"DESKTOP-3OVO59V\\\"]\",\"oldValue\":\"[\\\"MGPfnTFZcpacjK3\\\"]\"},{\"displayName\":\"testValue4\",\"newValue\":\"[\\\"1.0\\\"]\",\"oldValue\":\"[\\\"10.0.22631.2715\\\"]\"},{\"displayName\":\"testValue5\",\"newValue\":\"[\\\"DESKTOP-3OVO59V\\\"]\",\"oldValue\":\"[\\\"MGPfnTFZcpacjK3\\\"]\"},{\"displayName\":\"testValue6\",\"newValue\":\"\\\"CloudDeviceOSVersion, CloudDisplayName, DeviceOSVersion, DisplayName\\\"\"},{\"displayName\":\"testValue7\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue8\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue9\",\"newValue\":\"\\\"AzureAd\\\"\"},{\"displayName\":\"testValue10\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue11\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:42:30.543541Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_Y07Z6_76707176\",\"activityDateTime\":\"2025-11-12T14:03:30.215713+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"ServerAd\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"ServerAd\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:03:30.215713Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_Y07Z6_76707187\",\"activityDateTime\":\"2025-11-12T14:03:30.218714+00:00\",\"activityDisplayName\":\"Add registered owner to device\",\"additionalDetails\":[],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Assign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"MGPWZXVdvYvPPHl\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"},{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Device\"}]}",
"event": {
"action": "Add registered owner to device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:03:30.218714Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue2",
"newValue": "\"00000000-0000-0000-0000-000000000000\""
},
{
"displayName": "testValue3",
"newValue": "\"MGPWZXVdvYvPPHl\""
}
],
"operationType": "Assign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_2U6UD_333241557\",\"activityDateTime\":\"2025-11-12T13:45:54.725625+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"AzureAd\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"MGPWZXVdvYvPPHl\\\"]\",\"oldValue\":\"[\\\"DESKTOP-3OVO59V\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"[\\\"MGPWZXVdvYvPPHl\\\"]\",\"oldValue\":\"[\\\"DESKTOP-3OVO59V\\\"]\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"CloudDisplayName, DisplayName\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue6\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue7\",\"newValue\":\"\\\"AzureAd\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:45:54.725625Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_8PB2D_179417222\",\"activityDateTime\":\"2025-11-12T14:03:30.275227+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"ServerAd\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[true]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue3\",\"newValue\":\"[true]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"IsCompliant, IsManaged\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue6\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue7\",\"newValue\":\"\\\"ServerAd\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:03:30.275227Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_JKBFB_24708374\",\"activityDateTime\":\"2025-11-12T13:59:30.466523+00:00\",\"activityDisplayName\":\"Update group\",\"additionalDetails\":[{\"key\":\"GroupType\",\"value\":\"\"}],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"group1\",\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:59:30Z\\\"]\",\"oldValue\":\"[\\\"2025-11-04T13:32:33Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"\\\"\"}],\"type\":\"Group\"}]}",
"event": {
"action": "Update group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:59:30.466523Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_AKO2H_321268711\",\"activityDateTime\":\"2025-11-12T13:41:07.443987+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"ServerAd\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"ServerAd\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:41:07.443987Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_B2WA2_60110657\",\"activityDateTime\":\"2025-11-12T13:29:29.313351+00:00\",\"activityDisplayName\":\"Update group\",\"additionalDetails\":[{\"key\":\"GroupType\",\"value\":\"\"}],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"group1\",\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:29Z\\\"]\",\"oldValue\":\"[\\\"2025-11-10T10:24:14Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"\\\"\"}],\"type\":\"Group\"}]}",
"event": {
"action": "Update group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.313351Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_B2WA2_60110707\",\"activityDateTime\":\"2025-11-12T13:29:29.341356+00:00\",\"activityDisplayName\":\"Update group\",\"additionalDetails\":[{\"key\":\"GroupType\",\"value\":\"\"}],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"group1\",\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:29Z\\\"]\",\"oldValue\":\"[\\\"2025-06-05T08:16:43Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"\\\"\"}],\"type\":\"Group\"}]}",
"event": {
"action": "Update group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.341356Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_B2WA2_60110730\",\"activityDateTime\":\"2025-11-12T13:29:29.356351+00:00\",\"activityDisplayName\":\"Update group\",\"additionalDetails\":[{\"key\":\"GroupType\",\"value\":\"\"}],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"group1\",\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:29Z\\\"]\",\"oldValue\":\"[\\\"2025-10-20T08:51:54Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"\\\"\"}],\"type\":\"Group\"}]}",
"event": {
"action": "Update group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.356351Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232454\",\"activityDateTime\":\"2025-11-12T13:29:28.930924+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T11:59:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:28.930924Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T11:59:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232475\",\"activityDateTime\":\"2025-11-12T13:29:28.938929+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T10:59:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:28.938929Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T10:59:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232483\",\"activityDateTime\":\"2025-11-12T13:29:28.946929+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T12:59:28Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:28.946929Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T12:59:28Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232510\",\"activityDateTime\":\"2025-11-12T13:29:28.961923+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T10:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:28.961923Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T10:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232546\",\"activityDateTime\":\"2025-11-12T13:29:28.983926+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-10T15:54:14Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:28.983926Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-10T15:54:14Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232570\",\"activityDateTime\":\"2025-11-12T13:29:28.997930+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T09:23:11Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:28.997930Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T09:23:11Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232578\",\"activityDateTime\":\"2025-11-12T13:29:29.022929+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T10:59:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.022929Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T10:59:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232587\",\"activityDateTime\":\"2025-11-12T13:29:29.032924+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T12:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.032924Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T12:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232595\",\"activityDateTime\":\"2025-11-12T13:29:29.043929+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T09:52:04Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.043929Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T09:52:04Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232603\",\"activityDateTime\":\"2025-11-12T13:29:29.053924+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T09:52:04Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.053924Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T09:52:04Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232611\",\"activityDateTime\":\"2025-11-12T13:29:29.064925+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T12:59:28Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.064925Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T12:59:28Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232619\",\"activityDateTime\":\"2025-11-12T13:29:29.072925+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T12:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.072925Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T12:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232627\",\"activityDateTime\":\"2025-11-12T13:29:29.090923+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T08:53:09Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.090923Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T08:53:09Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232635\",\"activityDateTime\":\"2025-11-12T13:29:29.101926+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T08:53:09Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.101926Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T08:53:09Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232643\",\"activityDateTime\":\"2025-11-12T13:29:29.110931+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T11:59:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.110931Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T11:59:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232651\",\"activityDateTime\":\"2025-11-12T13:29:29.118931+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T10:59:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.118931Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T10:59:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232659\",\"activityDateTime\":\"2025-11-12T13:29:29.128932+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-12T11:29:27Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.128932Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-12T11:29:27Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232682\",\"activityDateTime\":\"2025-11-12T13:29:29.139923+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-10T11:24:12Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.139923Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-10T11:24:12Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_testestest_HJLSQ_47232724\",\"activityDateTime\":\"2025-11-12T13:29:29.149926+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"testestest\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"2025-11-12T13:29:28Z\\\"]\",\"oldValue\":\"[\\\"2025-11-07T14:53:10Z\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"LastDirSyncTime\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"DirectorySync\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:29:29.149926Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"LastDirSyncTime\""
},
{
"displayName": "testValue4",
"newValue": "\"DirectorySync\""
},
{
"displayName": "testValue5",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[\"2025-11-12T13:29:28Z\"]",
"oldValue": "[\"2025-11-07T14:53:10Z\"]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "testestest"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_CJDR7_469136918\",\"activityDateTime\":\"2025-11-12T14:03:30.128988+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"ServerAd\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"10.0.22631.2715\\\"]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"DeviceOSVersion\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue6\",\"newValue\":\"\\\"ServerAd\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:03:30.128988Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_2TU5W_349622662\",\"activityDateTime\":\"2025-11-12T13:35:53.640611+00:00\",\"activityDisplayName\":\"Update user\",\"additionalDetails\":[{\"key\":\"UserType\",\"value\":\"Member\"}],\"category\":\"UserManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[{\\\"DeviceName\\\":\\\"SM-A546B\\\",\\\"DeviceToken\\\":\\\"e7KRRYuURkCnbhP4qs6Hf-:APA91bFWzlbY1c58DSgwNdxi35vrKZy_1r4RHbDRrdhzMv5xXw_kMnZ1WFgPS1KJy3NXTNIqEkmEhm0yLeeYGs7aSG8WC1HGecy7L8UJZ7eWR3gELgP9nDE9biLqzpxBg00FWpUhhc6N\\\",\\\"DeviceTag\\\":\\\"SoftwareTokenActivated\\\",\\\"PhoneAppVersion\\\":\\\"6.2510.7126\\\",\\\"OathTokenTimeDrift\\\":3,\\\"DeviceId\\\":\\\"00000000-0000-0000-0000-000000000000\\\",\\\"Id\\\":\\\"00000000-0000-0000-0000-000000000000\\\",\\\"TimeInterval\\\":0,\\\"AuthenticationType\\\":3,\\\"NotificationType\\\":4,\\\"LastAuthenticatedTimestamp\\\":\\\"2025-11-12T06:39:44.42863Z\\\",\\\"AuthenticatorFlavor\\\":\\\"Authenticator\\\",\\\"HashFunction\\\":null,\\\"TenantDeviceId\\\":null,\\\"SecuredPartitionId\\\":20115,\\\"SecuredKeyId\\\":7}]\",\"oldValue\":\"[{\\\"DeviceName\\\":\\\"SM-A546B\\\",\\\"DeviceToken\\\":\\\"e7KRRYuURkCnbhP4qs6Hf-:APA91bFWzlbY1c58DSgwNdxi35vrKZy_1r4RHbDRrdhzMv5xXw_kMnZ1WFgPS1KJy3NXTNIqEkmEhm0yLeeYGs7aSG8WC1HGecy7L8UJZ7eWR3gELgP9nDE9biLqzpxBg00FWpUhhc6N\\\",\\\"DeviceTag\\\":\\\"SoftwareTokenActivated\\\",\\\"PhoneAppVersion\\\":\\\"6.2510.7126\\\",\\\"OathTokenTimeDrift\\\":2,\\\"DeviceId\\\":\\\"00000000-0000-0000-0000-000000000000\\\",\\\"Id\\\":\\\"00000000-0000-0000-0000-000000000000\\\",\\\"TimeInterval\\\":0,\\\"AuthenticationType\\\":3,\\\"NotificationType\\\":4,\\\"LastAuthenticatedTimestamp\\\":\\\"2025-11-12T06:39:44.42863Z\\\",\\\"AuthenticatorFlavor\\\":\\\"Authenticator\\\",\\\"HashFunction\\\":null,\\\"TenantDeviceId\\\":null,\\\"SecuredPartitionId\\\":20115,\\\"SecuredKeyId\\\":7}]\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"StrongAuthenticationPhoneAppDetail\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"Member\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}]}",
"event": {
"action": "Update user",
"dataset": "UserManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:35:53.640611Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue3",
"newValue": "\"StrongAuthenticationPhoneAppDetail\""
},
{
"displayName": "testValue4",
"newValue": "\"Member\""
},
{
"displayName": "testValue2",
"newValue": "[{\"DeviceName\":\"SM-A546B\",\"DeviceToken\":\"e7KRRYuURkCnbhP4qs6Hf-:APA91bFWzlbY1c58DSgwNdxi35vrKZy_1r4RHbDRrdhzMv5xXw_kMnZ1WFgPS1KJy3NXTNIqEkmEhm0yLeeYGs7aSG8WC1HGecy7L8UJZ7eWR3gELgP9nDE9biLqzpxBg00FWpUhhc6N\",\"DeviceTag\":\"SoftwareTokenActivated\",\"PhoneAppVersion\":\"6.2510.7126\",\"OathTokenTimeDrift\":3,\"DeviceId\":\"00000000-0000-0000-0000-000000000000\",\"Id\":\"00000000-0000-0000-0000-000000000000\",\"TimeInterval\":0,\"AuthenticationType\":3,\"NotificationType\":4,\"LastAuthenticatedTimestamp\":\"2025-11-12T06:39:44.42863Z\",\"AuthenticatorFlavor\":\"Authenticator\",\"HashFunction\":null,\"TenantDeviceId\":null,\"SecuredPartitionId\":20115,\"SecuredKeyId\":7}]",
"oldValue": "[{\"DeviceName\":\"SM-A546B\",\"DeviceToken\":\"e7KRRYuURkCnbhP4qs6Hf-:APA91bFWzlbY1c58DSgwNdxi35vrKZy_1r4RHbDRrdhzMv5xXw_kMnZ1WFgPS1KJy3NXTNIqEkmEhm0yLeeYGs7aSG8WC1HGecy7L8UJZ7eWR3gELgP9nDE9biLqzpxBg00FWpUhhc6N\",\"DeviceTag\":\"SoftwareTokenActivated\",\"PhoneAppVersion\":\"6.2510.7126\",\"OathTokenTimeDrift\":2,\"DeviceId\":\"00000000-0000-0000-0000-000000000000\",\"Id\":\"00000000-0000-0000-0000-000000000000\",\"TimeInterval\":0,\"AuthenticationType\":3,\"NotificationType\":4,\"LastAuthenticatedTimestamp\":\"2025-11-12T06:39:44.42863Z\",\"AuthenticatorFlavor\":\"Authenticator\",\"HashFunction\":null,\"TenantDeviceId\":null,\"SecuredPartitionId\":20115,\"SecuredKeyId\":7}]"
}
],
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_HGAF2_134745489\",\"activityDateTime\":\"2025-11-12T14:04:58.356854+00:00\",\"activityDisplayName\":\"Add member to group\",\"additionalDetails\":[],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Assign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"GS_DYN_INTUNE_HP\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"}],\"type\":\"Device\"},{\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Group\"}]}",
"event": {
"action": "Add member to group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:04:58.356854Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Assign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_HGAF2_134745514\",\"activityDateTime\":\"2025-11-12T14:04:58.357853+00:00\",\"activityDisplayName\":\"Remove member from group\",\"additionalDetails\":[],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Unassign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"oldValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"oldValue\":\"\\\"GS_DYN_INTUNE_HP\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"}],\"type\":\"Device\"},{\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Group\"}]}",
"event": {
"action": "Remove member from group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:04:58.357853Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Unassign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_YH1R3_393146797\",\"activityDateTime\":\"2025-11-12T13:40:57.356395+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"ServerAd\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"ServerAd\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:40:57.356395Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_EAN4D_643720908\",\"activityDateTime\":\"2025-11-12T14:03:24.654184+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"ServerAd\"},{\"key\":\"User-Agent\",\"value\":\"Microsoft.OData.Client/7.12.5\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"10.0.22631.2715\\\"]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue3\",\"newValue\":\"[\\\"[HWID]:h:6755471819947872\\\",\\\"[USER-HWID]:00000000-0000-0000-0000-000000000000:6755471819947872\\\",\\\"[GID]:g:6755498089741506\\\",\\\"[USER-GID]:00000000-0000-0000-0000-000000000000:6755498089741506\\\",\\\"[ZTDID]:00000000-0000-0000-0000-000000000000\\\",\\\"[PurchaseOrderId]:Unknown\\\"]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue4\",\"newValue\":\"[true]\",\"oldValue\":\"[]\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"DeviceOSVersion, DevicePhysicalIds, IsManaged\\\"\"},{\"displayName\":\"testValue6\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue7\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue8\",\"newValue\":\"\\\"ServerAd\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:03:24.654184Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_LBGG3_589281889\",\"activityDateTime\":\"2025-11-12T14:03:30.351306+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"ServerAd\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"ServerAd\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:03:30.351306Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_LBGG3_589281902\",\"activityDateTime\":\"2025-11-12T14:03:30.354309+00:00\",\"activityDisplayName\":\"Add registered users to device\",\"additionalDetails\":[],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Assign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"MGPWZXVdvYvPPHl\\\"\"}],\"type\":\"User\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"},{\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Device\"}]}",
"event": {
"action": "Add registered users to device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:03:30.354309Z",
"azure": {
"entraid": {
"properties": {
"modifiedProperties": [
{
"displayName": "testValue2",
"newValue": "\"00000000-0000-0000-0000-000000000000\""
},
{
"displayName": "testValue3",
"newValue": "\"MGPWZXVdvYvPPHl\""
}
],
"operationType": "Assign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_S31E7_413742199\",\"activityDateTime\":\"2025-11-12T14:04:58.365644+00:00\",\"activityDisplayName\":\"Add member to group\",\"additionalDetails\":[],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Assign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"GS_DYN_INTUNE_LAPTOPS\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"}],\"type\":\"Device\"},{\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Group\"}]}",
"event": {
"action": "Add member to group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:04:58.365644Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Assign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_S31E7_413742214\",\"activityDateTime\":\"2025-11-12T14:04:58.366643+00:00\",\"activityDisplayName\":\"Remove member from group\",\"additionalDetails\":[],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Unassign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"oldValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"oldValue\":\"\\\"GS_DYN_INTUNE_LAPTOPS\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"}],\"type\":\"Device\"},{\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Group\"}]}",
"event": {
"action": "Remove member from group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:04:58.366643Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Unassign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_S31E7_413742523\",\"activityDateTime\":\"2025-11-12T14:04:58.426647+00:00\",\"activityDisplayName\":\"Add member to group\",\"additionalDetails\":[],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Assign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"GS_DYN_INTUNE_AUTOPILOT\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"}],\"type\":\"Device\"},{\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Group\"}]}",
"event": {
"action": "Add member to group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:04:58.426647Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Assign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_S31E7_413742903\",\"activityDateTime\":\"2025-11-12T14:04:58.507645+00:00\",\"activityDisplayName\":\"Add member to group\",\"additionalDetails\":[],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Assign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"GS_INTUNE_ASR\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"}],\"type\":\"Device\"},{\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Group\"}]}",
"event": {
"action": "Add member to group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:04:58.507645Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Assign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_S31E7_413742918\",\"activityDateTime\":\"2025-11-12T14:04:58.508648+00:00\",\"activityDisplayName\":\"Remove member from group\",\"additionalDetails\":[],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Unassign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"oldValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"oldValue\":\"\\\"GS_INTUNE_ASR\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"}],\"type\":\"Device\"},{\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Group\"}]}",
"event": {
"action": "Remove member from group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:04:58.508648Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Unassign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_S31E7_413743167\",\"activityDateTime\":\"2025-11-12T14:04:58.557645+00:00\",\"activityDisplayName\":\"Add member to group\",\"additionalDetails\":[],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Assign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"GS_DYN_INTUNE_WINDOWS_CLIENT\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"}],\"type\":\"Device\"},{\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Group\"}]}",
"event": {
"action": "Add member to group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:04:58.557645Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Assign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_S31E7_413743350\",\"activityDateTime\":\"2025-11-12T14:04:58.637647+00:00\",\"activityDisplayName\":\"Add member to group\",\"additionalDetails\":[],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Assign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"newValue\":\"\\\"GS_DYN_WINDOWS_CLIENT\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"}],\"type\":\"Device\"},{\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Group\"}]}",
"event": {
"action": "Add member to group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:04:58.637647Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Assign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_S31E7_413743373\",\"activityDateTime\":\"2025-11-12T14:04:58.639645+00:00\",\"activityDisplayName\":\"Remove member from group\",\"additionalDetails\":[],\"category\":\"GroupManagement\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Unassign\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"oldValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue3\",\"oldValue\":\"\\\"GS_DYN_WINDOWS_CLIENT\\\"\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"https://approvalmanagement.activedirectory.windowsazure.com;00000000-0000-0000-0000-000000000000;00000000-0000-0000-0000-000000000000/approvalmanagement.activedirectory.windowsazure.com\\\"\"}],\"type\":\"Device\"},{\"groupType\":\"unknownFutureValue\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[],\"type\":\"Group\"}]}",
"event": {
"action": "Remove member from group",
"dataset": "GroupManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T14:04:58.639645Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Unassign"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_00000000-0000-0000-0000-000000000000_J83GJ_537583264\",\"activityDateTime\":\"2025-11-12T13:43:48.788078+00:00\",\"activityDisplayName\":\"Update device\",\"additionalDetails\":[{\"key\":\"DeviceId\",\"value\":\"00000000-0000-0000-0000-000000000000\"},{\"key\":\"DeviceOSType\",\"value\":\"Windows\"},{\"key\":\"DeviceTrustType\",\"value\":\"AzureAd\"}],\"category\":\"Device\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"initiatedBy\":{\"app\":{\"displayName\":\"testValue1\",\"servicePrincipalId\":\"00000000-0000-0000-0000-000000000000\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Update\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"example.com\",\"id\":\"00000000-0000-0000-0000-000000000000\",\"modifiedProperties\":[{\"displayName\":\"testValue2\",\"newValue\":\"[\\\"10.0.22631.2715\\\"]\",\"oldValue\":\"[\\\"1.0\\\"]\"},{\"displayName\":\"testValue3\",\"newValue\":\"[\\\"10.0.22631.2715\\\"]\",\"oldValue\":\"[\\\"1.0\\\"]\"},{\"displayName\":\"testValue4\",\"newValue\":\"\\\"CloudDeviceOSVersion, DeviceOSVersion\\\"\"},{\"displayName\":\"testValue5\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue6\",\"newValue\":\"\\\"Windows\\\"\"},{\"displayName\":\"testValue7\",\"newValue\":\"\\\"AzureAd\\\"\"},{\"displayName\":\"testValue8\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"},{\"displayName\":\"testValue9\",\"newValue\":\"\\\"00000000-0000-0000-0000-000000000000\\\"\"}],\"type\":\"Device\"}]}",
"event": {
"action": "Update device",
"dataset": "Device",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-12T13:43:48.788078Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Update"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"host": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "example.com"
},
"service": {
"name": "Core Directory"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
}
}
{
"message": "{\"id\":\"Directory_000000-000000000-000000-0000000\",\"activityDateTime\":\"2025-11-25T10:52:22.177578+00:00\",\"activityDisplayName\":\"Create application \\u2013 Certificates and secrets management \",\"additionalDetails\":[{\"key\":\"User-Agent\",\"value\":\"O365AdminPortal\"},{\"key\":\"AppId\",\"value\":\"TEST-APP-ID\"}],\"category\":\"ApplicationManagement\",\"correlationId\":\"TEST-CORRELATION-ID\",\"initiatedBy\":{\"user\":{\"displayName\":\"user1\",\"id\":\"user1\",\"@odata.type\":\"#microsoft.graph.userIdentity\",\"userType\":null,\"agentType\":\"notAgentic\",\"homeTenantId\":null,\"homeTenantName\":null,\"ipAddress\":\"192.0.2.1\",\"userPrincipalName\":\"ANONYMIZED_VALUE\"}},\"loggedByService\":\"Core Directory\",\"operationType\":\"Add\",\"result\":\"success\",\"resultReason\":\"\",\"targetResources\":[{\"displayName\":\"ChatGPT for Excel\",\"id\":\"TEST-SERVICE-ID\",\"modifiedProperties\":[{\"displayName\":\"KeyDescription\",\"newValue\":\"[]\",\"oldValue\":\"[]\"},{\"displayName\":\"Included Updated Properties\",\"newValue\":\"\\\"KeyDescription\\\"\"}],\"type\":\"Application\"}]}",
"event": {
"action": "Create application \u2013 Certificates and secrets management ",
"dataset": "ApplicationManagement",
"outcome": "success",
"provider": "Core Directory"
},
"@timestamp": "2025-11-25T10:52:22.177578Z",
"azure": {
"entraid": {
"properties": {
"operationType": "Add"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"related": {
"ip": [
"192.0.2.1"
],
"user": [
"user1"
]
},
"service": {
"id": "TEST-SERVICE-ID",
"name": "ChatGPT for Excel"
},
"source": {
"address": "192.0.2.1",
"ip": "192.0.2.1"
},
"trace": {
"id": "TEST-CORRELATION-ID"
},
"user": {
"email": "ANONYMIZED_VALUE",
"id": "user1",
"name": "user1"
}
}
{
"message": "{\"id\":\"00000000-0000-0000-0000-000000000000\",\"createdDateTime\":\"2023-12-01T16:03:35Z\",\"userDisplayName\":\"user1\",\"userPrincipalName\":\"ANONYMIZED_VALUE\",\"userId\":\"user1\",\"appId\":\"00000000-0000-0000-0000-000000000000\",\"appDisplayName\":\"Graph explorer\",\"ipAddress\":\"192.0.2.1\",\"clientAppUsed\":\"Browser\",\"correlationId\":\"00000000-0000-0000-0000-000000000000\",\"conditionalAccessStatus\":\"notApplied\",\"isInteractive\":true,\"riskDetail\":\"none\",\"riskLevelAggregated\":\"none\",\"riskLevelDuringSignIn\":\"none\",\"riskState\":\"none\",\"riskEventTypes\":[],\"resourceDisplayName\":\"Microsoft Graph\",\"resourceId\":\"00000000-0000-0000-0000-000000000000\",\"status\":{\"errorCode\":0,\"failureReason\":\"Test failure reason\",\"additionalDetails\":null},\"deviceDetail\":{\"deviceId\":\"\",\"displayName\":null,\"operatingSystem\":\"example.com\",\"browser\":\"Edge 80.0.361\",\"isCompliant\":null,\"isManaged\":null,\"trustType\":null},\"location\":{\"city\":\"Redmond\",\"state\":\"Washington\",\"countryOrRegion\":\"US\",\"geoCoordinates\":{\"altitude\":null,\"latitude\":47.68050003051758,\"longitude\":-122.12094116210938}},\"appliedConditionalAccessPolicies\":[{\"id\":\"00000000-0000-0000-0000-000000000000\",\"displayName\":\"testValue1\",\"enforcedGrantControls\":[],\"enforcedSessionControls\":[],\"result\":\"notEnabled\"},{\"id\":\"00000000-0000-0000-0000-000000000000\",\"displayName\":\"testValue2\",\"enforcedGrantControls\":[],\"enforcedSessionControls\":[],\"result\":\"notEnabled\"}]}",
"event": {
"code": "0",
"provider": "Microsoft Graph"
},
"@timestamp": "2023-12-01T16:03:35Z",
"azure": {
"entraid": {
"properties": {
"appliedConditionalAccessPolicies": [
{
"displayName": "testValue1",
"enforcedGrantControls": [],
"enforcedSessionControls": [],
"id": "00000000-0000-0000-0000-000000000000",
"result": "notEnabled"
},
{
"displayName": "testValue2",
"enforcedGrantControls": [],
"enforcedSessionControls": [],
"id": "00000000-0000-0000-0000-000000000000",
"result": "notEnabled"
}
],
"clientAppUsed": "Browser",
"conditionalAccessStatus": "notApplied",
"isInteractive": "true",
"resourceId": "00000000-0000-0000-0000-000000000000",
"riskDetail": "none",
"riskEventTypes": [],
"riskLevelAggregated": "none",
"riskLevelDuringSignIn": "none",
"riskState": "none"
}
}
},
"cloud": {
"provider": "Azure",
"service": {
"name": "Azure EntraId"
}
},
"error": {
"message": "Test failure reason"
},
"host": {
"os": {
"name": "example.com"
}
},
"related": {
"ip": [
"192.0.2.1"
],
"user": [
"user1"
]
},
"service": {
"id": "00000000-0000-0000-0000-000000000000",
"name": "Graph explorer"
},
"source": {
"address": "192.0.2.1",
"geo": {
"city_name": "Redmond",
"country_iso_code": "US",
"location": {
"lat": 47.68050003051758,
"lon": -122.12094116210938
},
"region_name": "Washington"
},
"ip": "192.0.2.1"
},
"trace": {
"id": "00000000-0000-0000-0000-000000000000"
},
"user": {
"email": "ANONYMIZED_VALUE",
"id": "user1",
"name": "user1"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "Edge 80.0.361",
"os": {
"name": "Other"
}
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
@timestamp |
date |
Date/time when the event originated. |
azure.entraid.properties.appliedConditionalAccessPolicies |
array |
|
azure.entraid.properties.clientAppUsed |
keyword |
|
azure.entraid.properties.conditionalAccessStatus |
keyword |
|
azure.entraid.properties.isInteractive |
keyword |
|
azure.entraid.properties.modifiedProperties |
array |
|
azure.entraid.properties.operationType |
keyword |
|
azure.entraid.properties.resourceId |
keyword |
|
azure.entraid.properties.riskDetail |
keyword |
|
azure.entraid.properties.riskEventTypes |
keyword |
|
azure.entraid.properties.riskLevelAggregated |
keyword |
|
azure.entraid.properties.riskLevelDuringSignIn |
keyword |
|
azure.entraid.properties.riskState |
keyword |
|
cloud.provider |
keyword |
Name of the cloud provider. |
cloud.service.name |
keyword |
The cloud service name. |
error.message |
match_only_text |
Error message. |
event.action |
keyword |
The action captured by the event. |
event.code |
keyword |
Identification code for this event. |
event.dataset |
keyword |
Name of the dataset. |
event.outcome |
keyword |
The outcome of the event. The lowest level categorization field in the hierarchy. |
event.provider |
keyword |
Source of the event. |
event.reason |
keyword |
Reason why this event happened, according to the source |
host.id |
keyword |
Unique host id. |
host.name |
keyword |
Name of the host. |
host.os.name |
keyword |
Operating system name, without the version. |
service.id |
keyword |
Unique identifier of the running service. |
service.name |
keyword |
Name of the service. |
source.geo.city_name |
keyword |
City name. |
source.geo.country_iso_code |
keyword |
Country ISO code. |
source.geo.region_name |
keyword |
Region name. |
source.ip |
ip |
IP address of the source. |
trace.id |
keyword |
Unique identifier of the trace. |
user.email |
keyword |
User email address. |
user.id |
keyword |
Unique identifier of the user. |
user.name |
keyword |
Short name or login of the user. |
user_agent.original |
keyword |
Unparsed user_agent string. |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.